The number of disruptive and destructive global cyber-attacks taking place each year will increase by 105% to the end of 2024, according to a QBE report on Connected Business: digital dependency fuelling risk.
The trend shows these strategically significant, disruptive and destructive global cyber-attacks will more than double this year to 211, compared to 103 in 2020.

The NotPetya mass cyber-attack is one such example. It resulted in infections across Europe, North America and Asia Pacific. The associated NotPetya malware caused an estimated US$10bn in damages. These types of disruptive and destructive attacks are far rarer than data loss or simple device compromises type incidents that are in the 1000s or 10000s.
CrowdStrike’s failed update on 19 July 2024 cost Fortune 500 companies US$5.4bn in damages and US$25bn in share value. Cybercriminals were quick to exploit the event launching phishing campaigns with CrowdStrike-related lures, seeking to compromise systems, steal data and extort victims.
The number of ransomware attack victims will increase by 11% from 4,698 in 2023 to 5,200 in 2025, with manufacturing, healthcare, IT, education and government sectors particularly at risk. The average ransom payment in 2023 increased five-fold to USD$2m compared to USD$400,000 the previous year.
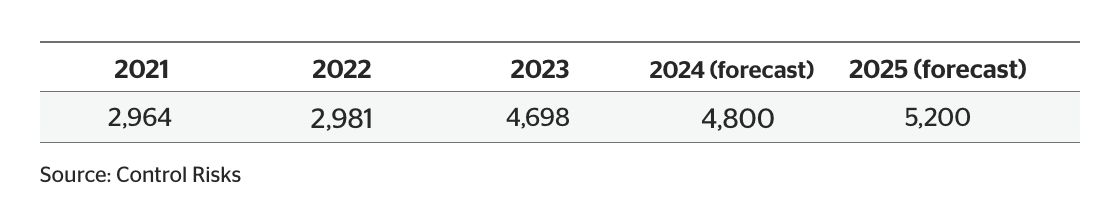
The full report, compiled by Control Risks for QBE, is available on the QBE website.
QBE’s 10 tips for businesses hit by a cyber-attack
- Contain the issue: isolate affected parts of the network to reduce the impact
- Evidence preservation: keep the network area running to retain critical evidence
- Evidence handling: avoid deleting or altering any information that could aid in incident investigations
- Notify your insurer’s breach response team
- Activate your incident response plan: notifying the crisis management team to ensure decisions can be made swiftly
- Think twice about paying ransoms: paying ransoms does not guarantee that data will be returned and can be illegal
- Communicate carefully with stakeholders: Ensure that accurate information is provided to manage expectations
- Identify the extent of the effect on suppliers, clients and other third parties
- Identify any deadlines that may be affected by the incident, such as payroll
- Regularly test your response plan against different breach scenarios.


